Step 10. Upload and deploy the updated companion.msi.
You can use the Package Manager feature in Management and Security Server to upload and then deploy the updated companion.msi with restricted settings to the end user workstation.
A. Upload the updated companion.msi file.
-
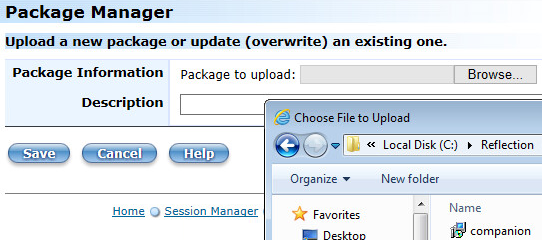
Open the Administrative WebStation, open Package Manager.
-
Click Add and then Browse to the companion.msi file that you created and updated on the administrative installation point. Select the file and click Open.
The default location is C:\Reflection\.
-
In Package Manager, note the file name on the “Package to upload:” line.
Enter a description and click Save to upload the package to the Administrative Server. Verify the package is included in the list.
Next, you will use Access Mapper to assign the package (with your updated companion.msi) to your domain user.
B. Deploy the updated companion.msi to the domain user.
Earlier, you used the Access Mapper to make a session available to the domain user. This time, you will use Access Mapper to “push” the modified companion package to the domain user.
-
In the Administrative WebStation, open Access Mapper.
-
As before, Search the LDAP directory for the domain user.
-
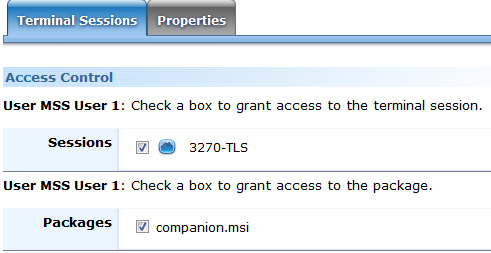
On the Terminal Sessions tab, verify that the correct user name is displayed.
-
In the Packages section, check companion.msi.
-
Click Save Settings (you may need to scroll) to deploy the package.
Now, when the domain user launches Reflection Workspace or a session, the package is downloaded, and the changes in the companion.msi are applied. The contents of the package are installed to the location specified in the .msi package.
Later, if you update the package (with the same file name), the newer one will be downloaded.
Review your progress
After updating the companion.msi with restricted security settings (Step 9) and deploying the msi package to the domain user (Step 10), you can now observe the “after” effect on the user’s restrictions.