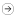The Security Proxy Server can be installed on the same computer as the Administrative Server or on a different computer. Although data between the terminal session and the Security Proxy server is encrypted, data between the Security Proxy server and the host computer is typically not encrypted.
No matter which installation method you choose, you can increase the security of terminal session connections by ensuring that there is only one known, secure link between the Security Proxy server and the host computer.
You may want to consider a dedicated connection between the Security Proxy server and the host computer, so that the Security Proxy server does not communicate with the host computer over a connection accessible by other computers on the network.
Another approach is to run the Security Proxy server directly on the host computer. A variety of platform-specific multi-component installation files for installing the Security Proxy are available that may be appropriate for your host. Replace the JRE with one that is appropriate for your host, if necessary.
If you run the Security Proxy server directly on the host computer, secure connections will be CPU- intensive because additional processing is required to encrypt and decrypt the data stream.
For more information see these technical notes:
1557: Security Proxy Server Performance Factors
1883: End-to-End Encryption through the Security Proxy
 previous
previous
 next
next