3.3 Lock Down the Workstation and Test the User Experience
In this section, you will lock down the user’s workstation by restricting the ability to change settings, and then deploying the updated package of security settings.
Steps in this section:
- Step 9. Update (modify) the security settings
- Step 10. Upload and deploy the updated companion.msi.
- Step 11. Test the domain user’s updated configuration.
________________________________________________________________________________
3.3.1 Step 9. Update (modify) the security settings.
The administrator can modify the existing companion.msi and “push” those restrictions to lock down the user’s workstation.
NOTE: You will use the Installation Customization Tool for all of Step 9.
A. Open the Installation Customization Tool, as before.
-
Log off Windows as the user; log on as the administrator.
-
Open the Installation Customization Tool, as before:
In the Windows Run line, enter C:\Reflection\setup.exe /admin
-
In the Select Customization dialog, select Open an existing Setup customization file or Companion installer. Click OK.

-
Select the companion msi that you previously customized.
B. Restrict the user from modifying the PAN Redaction Rules.
-
From the left nav, click Modify user settings.
-
From the list of Application – Settings, select Workspace Settings, and click Define.
-
In Reflection Workspace Settings under Trust Center, select Set Up Information Privacy.
-
Scroll to Primary Account Number (PAN) Redaction Rules, and check the first three boxes.

Click OK.
-
From the list of Application - Settings, select Reflection Desktop – application.access, and then click Define.

The Reflection Desktop Permissions Manager opens in a separate window. (There may be a pause.)
-
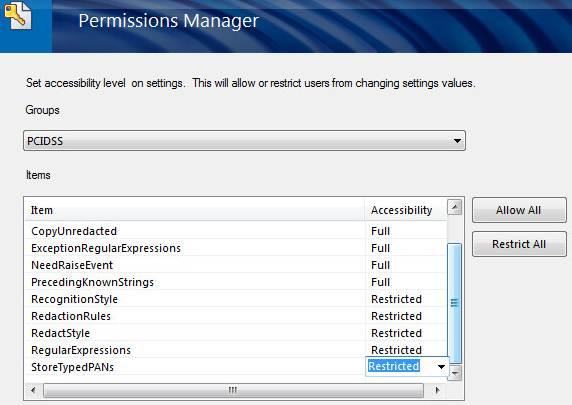
In the Groups drop-down menu, select PCIDSS.
-
Select these five items one at a time, and change the setting to Restricted for each. The “Restricted” setting requires an administrator logon to change the setting.
- RecognitionStyle
- RedactionRules
- RedactStyle
- RegularExpressions
- StoreTypedPANs
-
Click Next; then click Finish. Continue in the Installation Customization Tool
C. Restrict the user from modifying Centralized Management capabilities.
If Centralized Management is not enabled, the user’s workstation will no longer be managed by Management and Security Server, which defeats the administrator’s goal.
-
Select Reflection Desktop – application.access again, and click Define.
-
In the Permissions Manager Groups drop-down menu, select Centralized Management.
-
Select CentralizedManagementEnabled and change the setting to Restricted.
-
Select CentralizedManagementServerUrl, and change the setting to Restricted.

-
Click Next; then click Finish. Continue in the Installation Customization Tool.
D. Restrict the user’s ability to change the TLS settings.
-
Select Reflection Desktop-rd3x.access, and click Define.

-
In the Groups drop-down menu, select Document\Connection\TN3270Advanced.

-
On the right, click Restrict All. Click Next; then click Finish.
E. Save the companion file.
-
Click File > Save. Click Yes to increase the version number.
The new version number for the same file name will be recognized as a revision, and the resulting package will upgrade the previously deployed file.
-
Save the companion file using the same name. Click Yes to replace it and increase the version number.

-
Exit the Installation Customization Tool.
3.3.2 Step 10. Upload and deploy the updated companion.msi.
You can use Manage Packages in Management and Security Server to upload and then deploy the updated companion.msi with restricted settings to the end user workstation.
A. Upload the updated companion.msi file.
-
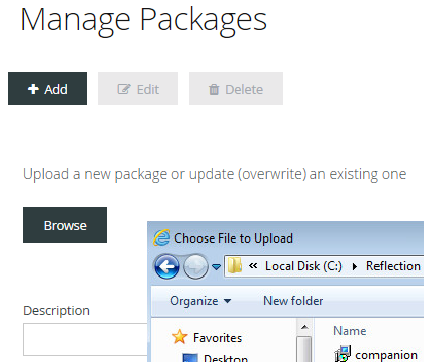
In Management and Security Server, open the Administrative Console to Manage Packages.
-
Click +Add and then Browse to the companion.msi file that you created and updated on the administrative installation point.
The default location is C:\Reflection\.
-
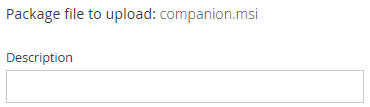
Click the companion.msi file and note the file name next to Package file to upload.
Enter a Description and click Save to upload the package to the Administrative Server. Verify the package is included in the list.
Next, you will return to Assign Access to assign the package (with your updated companion.msi) to your domain user.
B. Deploy the updated companion.msi to the domain user.
Earlier, you used Assign Access to make a session available to the domain user. This time, you will use Assign Access to “push” the modified companion package to the domain user.
-
In the Administrative Console, open Assign Access.
-
As before, Search the LDAP directory for the domain user.
-
On the right select Packages (instead of Sessions).
-
Verify that the correct user name is highlighted, and click check companion.msi.
-
Click Apply to deploy the package.
Now, when the domain user launches Reflection Workspace or a session, the package is downloaded, and the changes in the companion.msi are applied. The contents of the package are installed to the location specified in the .msi package.
Later, if you update the package (with the same file name), the newer one will be downloaded.
Review your progress
After updating the companion.msi with restricted security settings (Step 9) and deploying the msi package to the domain user (Step 10), you can now observe the “after” effect on the user’s restrictions.
3.3.3 Step 11. Test the domain user’s updated configuration.
-
Log off as the Windows administrator; log on as the domain user.
-
Launch the 3270-TLS session either in Recent Documents or by launching the product and the session.
-
NOTE: The settings for PAN Redaction Rules (Step 8: 4) are checked and cannot be changed without entering the administrator credentials.
-
NOTE: The TLS Connection settings (Step 8: 5) are restricted and cannot be changed by the domain user without entering administrator credentials.
Review your progress
Your test in Step 11 confirms that the company requirements to lock down the desktop are met:
-
Applications are hardened (locked down) to ensure company security mandates are enforced.
-
PCI compliance policies are enforced (with the PAN Redaction Rules).
-
Implementing centralized management and security does not disrupt the end-user experience.
________________________________________________________________________________
Related topic: